Recent Ransomware Attacks 2022.
This article covers 24 of the most recent ransomware attacks (so far) in 2022 — what they were and who they impacted — as well as some of the latest news and trends in ransomware attacks
Read our article on Eleven steps to preventing ransomware
IBM reports that ransomware attacks cost organizations an average of $4.62 million per breach in 2021 — a cost that doesn’t include the ransom demand itself!
Our article ‘Recent Ransomware Attacks 2022’ kicks off with a statistics list with a single number: $70 million.
This magic number represents the highest-known cryptocurrency ransom demand made by the Ransomware Evil (REvil) group in July 2021, according to CBS News. In the world’s most widespread ransomware attack, the attackers demanded $70 million in cryptocurrency in exchange for a universal software decryption key they claimed would decrypt all affected machines in 17 countries.
Revil (now Sodinokibi or, possibly, a new unnamed operation) is just one example of a ransomware variant that is prevalent in the wilds of the internet — and those are just one of the ones we know.
Ransomware are a type of cyberattack that occurs when malware is used to block companies and individuals from accessing their files, databases, and other computer systems until a ransom demand is paid.
Unfortunately without having proper defense mechanisms and response plans in place, ransomware attacks can cripple every type of organization —from small businesses to major organizations alike.
Ransomware Statistics You Should Know in 2022 and Beyond
These ransomware statistics cover everything from the direct costs of a ransomware attack to the indirect costs that stem from them in one way or another.
Even the methods these threat actors use vary from one to the next:
- Some ransomware attacks are the traditional extortion methods, which involve an attacker encrypting your data and forcing you to pay to obtain a decryption key to access the data.
- The next level of ransomware attacks involves an attacker exfiltrating your data as well. Once obtained, they’ll threaten to sell, leak, or publish it online if you don’t pay to keep it secret. An example of this was seen with the CL0p ransomware group.
1. $602 Million in Cryptocurrency Paid to Threat Actors in 2021
The 2022 Crypto Crime Report Chain analysis shows that $600+ million in cryptocurrency payments were made to ransomware attackers in 2021. Of course, the blockchain data research platform expects this number to grow throughout 2022 as more attacks and unknown payments become known over time.
As of Chainanalysis’s January 2022 report release, the 2021 payments came in well under the $692 million in payments that were given to attackers in 2020. (They originally reported $350 million but updated that number throughout 2021 as ransomware payments made in 2020 were discovered.)
2. Individual Ransomware Remands Skyrocket as Acer Reportedly Receives $50 Million Demand
Ransomware demands continue increasing year over year, coming with massive price tags. In March 2021, BleepingComputer reported Acer as receiving a $50 million ransom demand from the ransomware group REvil. That’s thought to be the highest ransomware demand to date with the previously known amount being $30 million in another REVil attack earlier in the year.
3. FBI Reports $49+ Million in Ransomware Adjusted Losses in 2021
Ransomware ranked one as one of the top cybercrime issues reported in 2021, according to the FBI Internet Crime Complaint Center’s (IC3) Internet Crime Report (2021). There were 3,729 complaints related to ransomware with adjusted losses exceeding $49 million.
This means that 1,255 more incidents were reported in 2021 than in 2020 with $20+ million in additional adjusted losses.
4. $590 Million in Ransomware-Related Activities Reported in First Half of 2021
The U.S. Treasury Department’s Financial Crimes Enforcement Network’s Financial Trend Analysis research shows that $590 million in suspicious activities were reported January-June 2021. (This is $70 million more than was reported in the entirety of 2020.) In that six-month time frame:
- 635 suspicious activity reports (SARs) were filed, and
- 458 transactions were reported.
5. Ransomware Victims Who Paid to Restore Their Encrypted Data Only Got 65% of It Back
Of course, not all ransomware-related costs are monetary. Nearly one-third (32%) of the 1,086 organizations Sophos surveyed for their 2021 State of Ransomware Report whose data was encrypted by attackers say that they paid their attackers. However, they typically received less than two-thirds of the data that was encrypted.
Ransomware Statistics: Most Popular Targets for Attackers
In this article ‘Recent Ransomware Attacks 2022’ it’s important to know the costs and objectives of ransomware attacks, it’s equally vital to know who or what they’re targeting in the first place. Short answer: bad guys will target anyone they want. But some specific industries make more tempting targets than others.
6. 60% of Ransomware-Related Breaches Involve Direct or Remote Malware Installation
Data from Verizon’s 2021 Data Breach Investigations Report (DBIR) shows that six in ten analyzed ransomware incidents involved either directly installed onto a machine or installed through remote desktop sharing apps.
Poor password management is something that can leave your organization’s remote desktop protocol vulnerable. Sophos’s 2022 Threat Report shares that “the root cause of many ransomware attacks is an initial access through a service that only requires a password.” By using passwordless authentication methods like client authentication certificates instead, you can avoid the issue of lost or stolen credentials altogether.
7. Everyone’s a Target: 71% of Surveyed Organizations Report Being Victimized by Ransomware Attacks
CyberEdge Group shares in their 2022 Cyberthreat Defense Report that nearly three-quarters of organizations report being victimized by ransomware attacks in the previous 12 months. The report also shows that ransomware is one of the top three cyberthreat concerns for businesses, ranking behind only account takeover/credential abuse attacks and other types of malicious software programs.
The report surveyed 1,200 IT security practitioners and decision-makers at 500+ employee organizations across seven industries in 17 countries.
8. 649 Critical Infrastructure Sector Organizations Targeted in 2021
The FBI IC3’s 2021 Internet Crime Report data shows that nearly 650 ransomware attacks targeted 16 critical infrastructure sectors last year. The three industries “leading” in terms of having the highest ransomware attacks are:
- Healthcare (148)
- Financial Services (89)
- Information Technology (74)
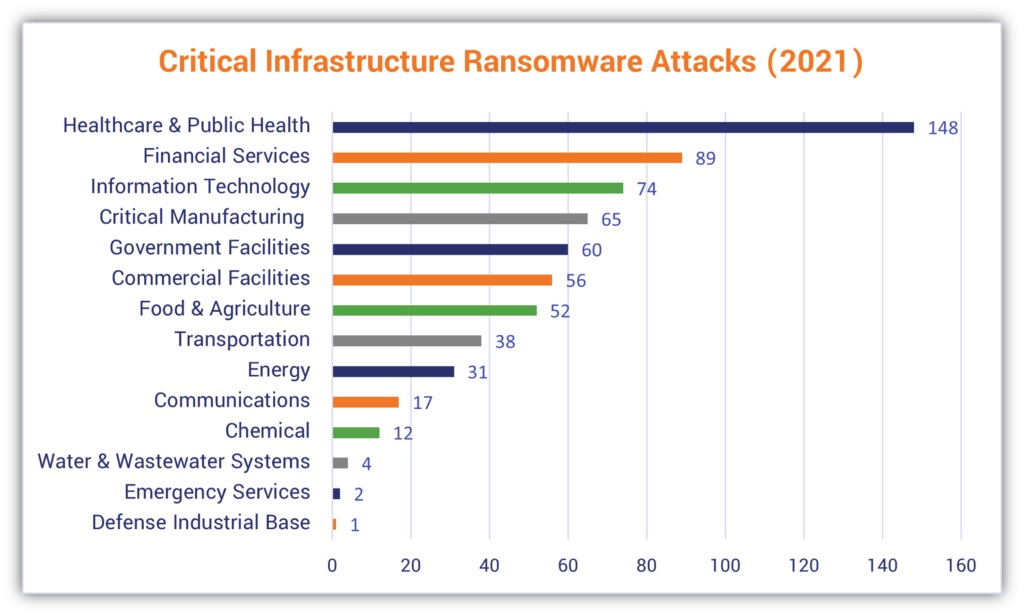
An example of a critical infrastructure-targeting attack (although not ransomware) was seen last year when a hacker breached a water treatment plant here in Florida. In April 2022, several federal agencies (FBI, CISA and NSA), combined with cybersecurity authorities in Canada, Australia, New Zealand, and the United Kingdom, released a joint advisory with mitigation guidance on how these types of organizations can make their networks more secure.
9. Ransomware Attacks on MSPs Jumped 105% Globally in 2021
It’s no secret that managed service providers (MSPs) make tempting targets for ransomware threat actors. Why? Because if an attacker can successfully infiltrate an MSP’s network or otherwise compromise their supply chains, they can use that access to increase their reach to their customers’ systems as well.
Sonicwall reports that global ransomware attacks surged to 623 million globally in 2021. This marks a 232% increase in ransomware since 2019. These attacks on U.K. targets increased 227%; for U.S. organizations, these attacks increased 98%.
A prime example of this was seen when the software company Kaseya found itself the target of a ransomware attack last summer. The company reported that up to 60 on-premises customers were MSPs who were infected via Kaseya’s hacked VSA remote monitoring and management software. This, in turn, affected upwards of 1,500 of the MSPs’ customers downstream.
Ransomware Statistics: A Look at Who Is Responsible for These Attacks
This next ransomware statistics section will explore what groups are responsible for many of the attacks you’ve seen in headlines over the last several years.
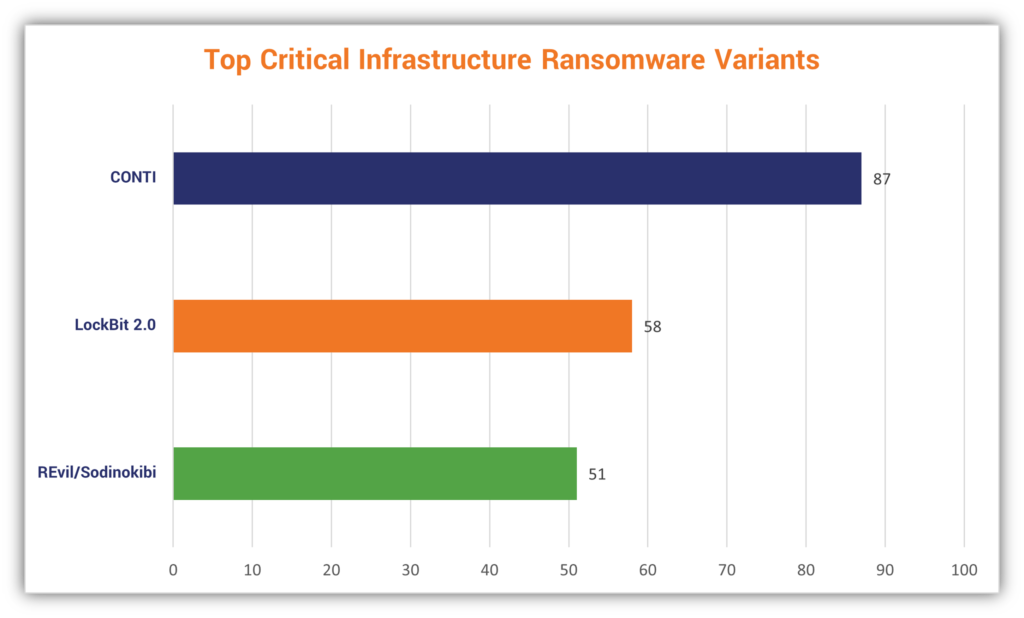
10. 196 Critical Infrastructure Attacks Were Carried Out By CONTI, LockBit20, and REvil/Sodinokibi
Ransomware attacks are thought to be largely underreported. The FBI IC3’s report shows that of the nearly 650 critical infrastructure attacks that took place in 2021, 196 of them were carried out by three ransomware groups.
11. 34% of MSP-Related Ransomware Attacks in 2021 Attributed to LockBit/LockBit 2.0
Earlier, we touched on how managed service providers are an attractive target for ransomware threat actors. Data from Connectwise’s 2022 MSP Threat Report shows that LockBit locks up rank No. 1 as the group that’s responsible for more than one-third of all ransomware attacks targeting MSPs in 2021. CONTI came in second place with 10%. The rest are attributed to a mishmash of other ransomware groups.
Ransomware Statistics: Types of Ransomware Attacks Methods and Tactics
Alright, now it’s time for a little something different with this article update. This time, we’re going to also talk about some of the specific tactics and approaches bad guys are taking to carry out ransomware attacks.
12. Sonicwall Reports Identifying an Average of 1,211 New Malware Variants Per Day
SonicWall Capture Labs reports that its Real-Time Deep Memory Inspection (RTDMI) technology identified “a total of 442,151 never-before-seen malware variants in 2021” — nearly a two-thirds (65%) year-over-year increase in new variants.
13. Conti V2 Variant Led the Way in 2021, Holding 19.4% of Ransomware Market Share
Data from Coveware’s Q4 2021 report shows that Conti V2 was the most common ransomware variant observed. Representing nearly 20% of the ransomware used in known attacks, it goes to show why CONTI and CONTI V2 continues to rank among the top ransomware groups. LockBit 2.0 and Hive hold the next highest market shares, coming in with 16.3% and 9.2%, respectively.
14. 54% of MSPs Rank Phishing Email as the Leading Attack Vector in SMB Ransomware Attacks
Ah, phishing — is a common theme in many of the articles we publish. Research from Datto’s 2020 State of the Channel Ransomware Report shows that more than half of the managed service provider survey respondents indicate that phishing emails are the biggest cause of ransomware attacks for SMBs. The next runners-up include:
- Poor user practices and gullibility (27%)
- Lack of cyber awareness and training (26%)
- Weak passwords and access management practices (21%)
15. EXOTIC LILY Attackers Impersonating Legitimate Businesses Send Up to 5,000 Emails Per Day
Speaking of phishing, Google’s Threat Analysis Group (TAG) shares that the ransomware group EXOTIC LILY uses social engineering and fake domains to spread human-operated ransomware via email. They’d register domains that are close to the real thing but have a different top-level domain (TLD) — for example, a bad guy would register “TheSSLStore.biz” or use another TLD if they wanted to impersonate “TheSSLstore.com.” After that, they’d use phishing tactics to get employees to click on malicious links containing malicious payloads that would exploit a Microsoft zero-day vulnerability (CVE-2021-40444).
According to Google TAG’s report:
“At the peak of EXOTIC LILY’s activity, we estimate they were sending more than 5,000 emails a day, to as many as 650 targeted organizations globally. Up until November 2021, the group seemed to be targeting specific industries such as IT, cybersecurity and healthcare, but as of late we have seen them attacking a wide variety of organizations and industries, with less specific focus.”
This underscores the importance of employee cyber-awareness training and public key infrastructure-based digital identity within organizations. There are several ways to add verifiable digital identities to your website and email domains.
- Installing an organization validated or extended validation website security certificate (SSL/TLS certificate) on your web servers enables you to display your site’s verified company information in your certificate details. This way, people know your website is legitimate and can differentiate it from other websites that don’t have your organization’s validated information in the certificate details.
- Using an email signing certificate (i.e., a S/MIME certificate) allows you to digitally sign emails so that recipients know your emails are authentic and haven’t been altered in any way.
- Implementing BIMI in combination with using a verified mark certificate (VMC) helps you to secure your domain against unauthorized usage. Using a VMC just goes to add additional identity by allowing you — and no one else — to display your organization’s verified company logo in recipients’ inboxes. (This has the added benefit of helping you brand your email.)
